- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Phrack Magazine: Digital hacking magazine.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
Tuesday, June 30, 2020
8 Hacking Websites & forums 2018 - Underground hacker sites
Thursday, June 11, 2020
DOWNLOAD NANOCORE RAT 1.2.2.0 CRACKED – REMOTE ADMINISTRATION TOOL
NanoCore is one of the most powerful RATs ever created. It is capable of taking complete control of a victim's machine. It allows a user to control the system with a Graphical User Interface (GUI). It has many features which allow a user to access remote computer as an administrator. Download nanocore rat 1.2.2.0 cracked version free of cost.
NanoCore's developer was arrested by FBI and pleaded guilty in 2017 for developing such a malicious privacy threat, and sentenced 33 months in prison.
FEATURES
- Complete Stealth Remote Control
- Recover Passwords from the Victim Device
- Manage Networks
- Manage Files
- Surveillance
- Plugins (To take it to the next level)
- Many advanced features like SCRIPTING
DOWNLOAD NANOCORE RAT 1.2.2.0 CRACKED – REMOTE ADMINISTRATION TOOL
ADVANTAGE OF ETHICAL HACKING
Advantage of Ethical Hacking
Hacking is quite useful in the following purpose-
1-To recover lost information, especially in case you lost your password.
2-To perform penetration testing to strengthen computer and network security.
3-To put adequate preventative measure in place to prevent security breaches.
4-To have a computer system that prevents malicious hackers from gaining access.
Hacking is quite useful in the following purpose-
1-To recover lost information, especially in case you lost your password.
2-To perform penetration testing to strengthen computer and network security.
3-To put adequate preventative measure in place to prevent security breaches.
4-To have a computer system that prevents malicious hackers from gaining access.
5-Fighting against terrorism and national security breaches.
More information
Wednesday, June 10, 2020
Ettercap: Man In The Middle (MITM)
 "Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
"Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
Website: http://ettercap.sourceforge.net
- Pentest Tools Github
- Hacking Site
- Hacking Lab
- Pentest Windows 7
- Hacker Kevin Mitnick
- How To Pentest A Website With Kali
- Pentest Vs Ceh
- Pentest Standard
- Hacking Browser
- Hackerrank Sql
- Pentest Free
- Pentest Certification
- Pentest+ Vs Ceh
- Pentest Active Directory
- Pentesting Tools
- How To Pentest A Network
- Hacking Vpn
- Hacking
- Hacker Videos
- Pentest Uk
How To Change Facebook’s Default Theme To Any Color You Want

How To Change Facebook's Default Theme To Any Color You Want
We are going to share an interesting trick on changing your Facebook default theme. You just need a Google Chrome extension to perform this trick. If you are among me who feels very fatigued with the look of Facebook's by default theme then this is a must-see post because you will find out the easiest trick to make your facebook more attractive than before.
Facebook is a social networking site which empowers people to connect with friends and people around. That's how Facebook is habitually introduced. However, Facebook is beyond the need of being introduced as almost everyone is on it.
A couple of Days ago I was simply Surfing Google Chrome website and I somehow stumbled upon a Chrome Extension. Yes, a Chrome extension that will give your Facebook a Whole new look. I was apprehensive to try it, So I just installed it and checked my facebook. I was astonished to see my facebook homepage have all new look. I found it refreshing and decided to write steps on How to Change Facebook Themes using Chrome Extension.
How To Change Facebook's Default Theme To Any Color You Want
If You are among me who feels very fatigued with the look of Facebook's by default theme then this is a must-see post, Because you will find out the easiest trick to make your facebook more attractive than before. Simply follow the steps to know about it.
How to Change Facebook Theme Using Chrome Extension
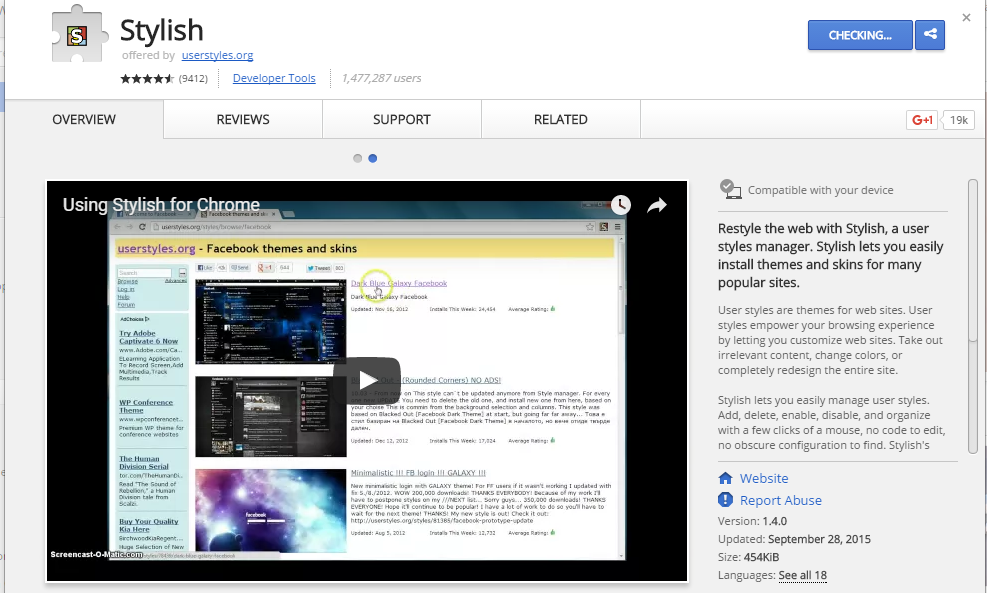
Step 1. Install Stylish for Chrome from the Chrome Web Store. It will take hardly a minute to get installed in your Chrome browser.
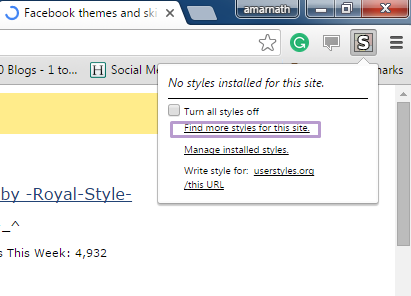
Step 2. Navigate to Facebook.com and click on the S button. Click on Find Styles for this Site to open a new tab with free themes to use for Facebook. Most of the themes are free and attractive too you can easily browse over the full website to discover your favorite theme.
Step 3. Now You will be redirected towards https://userstyles.org Guess what! This site contains huge numbers of Facebook themes, One thing is for sure that you will be confused in-between what to select and which one to skip. Select any them and click on it. Now you will be given a full preview of your selected theme.
Step 4. If everything is fine in the previewed theme, click on Install with Stylish button at the top right corner of the page. It will take few seconds or minutes depends on your theme size to be installed in Stylish Extension, once installed you will be notified with a success message.
Step 5. Now whenever you open Facebook, it will show the theme that you have installed with Stylish instead of the boring old blue theme.
More information
PHoss: A Password Sniffer
 "PHoss is a sniffer. A normal sniffer software is designed to find problems in data communication on the network. PHoss is designed to know some protocols which use (or may use) clear text passwords. Many protocols are designed to use secure authentication. For fallback they define a lowest level of authentication using clear text. Many companies use this lowest fallback definition as standard setting to make the product working in many environments." read more...
"PHoss is a sniffer. A normal sniffer software is designed to find problems in data communication on the network. PHoss is designed to know some protocols which use (or may use) clear text passwords. Many protocols are designed to use secure authentication. For fallback they define a lowest level of authentication using clear text. Many companies use this lowest fallback definition as standard setting to make the product working in many environments." read more...Download: http://www.phenoelit-us.org/phoss/download.html
"I Am Lady" Linux.Lady Trojan Samples
Bitcoin mining malware for Linux servers - samples
 Research: Dr. Web. Linux.Lady
Research: Dr. Web. Linux.LadySample Credit: Tim Strazzere
MD5 list:
0DE8BCA756744F7F2BDB732E3267C3F4
55952F4F41A184503C467141B6171BA7
86AC68E5B09D1C4B157193BB6CB34007
E2CACA9626ED93C3D137FDF494FDAE7C
E9423E072AD5A31A80A31FC1F525D614
Download. Email me if you need the password.
ShellForge
 "ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...
"ShellForge is a python program that builds shellcodes from C. It is inspired from Stealth's Hellkit. Some wrapper functions arround system calls are defined in header files. The C program uses them instead of libc calls. ShellForge uses gcc to convert it into assembler. It then modifies it a bit, compiles it, extract code from the object, may encode it and add a loader at the begining." read more...Related news
Pcap Of Wannacry Spreading Using EthernalBlue
Saw that a lot of people were looking for a pcap with WannaCry spreading Using EthernalBlue.
I have put together a little "petri dish" test environment and started looking for a sample that has the exploit. Some samples out there simply do not have the exploit code, and even tough they will encrypt the files locally, sometimes the mounted shares too, they would not spread.
Luckily, I have found this nice blog post from McAfee Labs: https://securingtomorrow.mcafee.com/mcafee-labs/analysis-wannacry-ransomware/ with the reference to the sample SHA256: 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c (they keep referring to samples with MD5, which is still a very-very bad practice, but the hash is MD5: DB349B97C37D22F5EA1D1841E3C89EB4)
Once I got the sample from the VxStream Sandbox site, dropped it in the test environment, and monitored it with Security Onion. I was super happy to see it spreading, despite the fact that for the first run my Windows 7 x64 VM went to BSOD as the EthernalBlue exploit failed.
But the second run was a full success, all my Windows 7 VMs got infected. Brad was so kind and made a guest blog post at one of my favorite sites, www.malware-traffic-analysis.net so you can find the pcap, description of the test environment and some screenshots here: http://malware-traffic-analysis.net/2017/05/18/index2.html
I have put together a little "petri dish" test environment and started looking for a sample that has the exploit. Some samples out there simply do not have the exploit code, and even tough they will encrypt the files locally, sometimes the mounted shares too, they would not spread.
Luckily, I have found this nice blog post from McAfee Labs: https://securingtomorrow.mcafee.com/mcafee-labs/analysis-wannacry-ransomware/ with the reference to the sample SHA256: 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c (they keep referring to samples with MD5, which is still a very-very bad practice, but the hash is MD5: DB349B97C37D22F5EA1D1841E3C89EB4)
Once I got the sample from the VxStream Sandbox site, dropped it in the test environment, and monitored it with Security Onion. I was super happy to see it spreading, despite the fact that for the first run my Windows 7 x64 VM went to BSOD as the EthernalBlue exploit failed.
But the second run was a full success, all my Windows 7 VMs got infected. Brad was so kind and made a guest blog post at one of my favorite sites, www.malware-traffic-analysis.net so you can find the pcap, description of the test environment and some screenshots here: http://malware-traffic-analysis.net/2017/05/18/index2.html
Related news
Magecart Targets Emergency Services-related Sites Via Insecure S3 Buckets
Hacking groups are continuing to leverage misconfigured AWS S3 data storage buckets to insert malicious code into websites in an attempt to swipe credit card information and carry out malvertising campaigns. In a new report shared with The Hacker News, cybersecurity firm RiskIQ said it identified three compromised websites belonging to Endeavor Business Media last month that are still hosting
via The Hacker News
via The Hacker News
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
Related articles
URLCrazy - Generate And Test Domain Typos And Variations To Detect And Perform Typo Squatting, URL Hijacking, Phishing, And Corporate Espionage
URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking, phishing, and corporate espionage.
Homepage: https://www.morningstarsecurity.com/research/urlcrazy
Use Cases
- Detect typo squatters profiting from typos on your domain name
- Protect your brand by registering popular typos
- Identify typo domain names that will receive traffic intended for another domain
- Conduct phishing attacks during a penetration test
Features
- Generates 15 types of domain variants
- Knows over 8000 common misspellings
- Supports bit flipping attacks
- Multiple keyboard layouts (qwerty, azerty, qwertz, dvorak)
- Checks if a domain variant is valid
- Test if domain variants are in use
- Estimate popularity of a domain variant
Installation
Install from a package manager
If you are using Kali Linux, Ubuntu or Debian use:
$ sudo apt install urlcrazyInstall latest release
Visit https://github.com/urbanadventurer/urlcrazy/releases
Install current development version
Be aware the latest development version may not be stable.
$ git clone https://github.com/urbanadventurer/urlcrazy.gitInstall Ruby
URLCrazy has been tested with Ruby versions 2.4 and 2.6.
If you are using Ubuntu or Debian use:
$ sudo apt install rubyInstall Bundler
Bundler provides dependecy management for Ruby projects
$ gem install bundlerInstall Dependencies
$ bundle installAlternatively, if you don't want to install bundler, the following command will install the gem dependencies.
$ gem install json colorize async async-dns async-httpUsage
Simple Usage
With default options, URLCrazy will check over 2000 typo variants for google.com.
$ urlcrazy google.comWith popularity estimate
$ urlcrazy -p domain.comCommandline Usage
Usage: ./urlcrazy [options] domain
Options
-k, --keyboard=LAYOUT Options are: qwerty, azerty, qwertz, dvorak (default: qwerty)
-p, --popularity Check domain popularity with Google
-r, --no-resolve Do not resolve DNS
-i, --show-invalid Show invalid domain names
-f, --format=TYPE Human readable or CSV (default: human readable)
-o, --output=FILE Output file
-n, --nocolor Disable colour
-h, --help This help
-v, --version Print version information. This version is 0.7Types of Domain Variations Supported
Character Omission
These typos are created by leaving out a letter of the domain name, one letter at a time. For example, www.goole.com and www.gogle.com
Character Repeat
These typos are created by repeating a letter of the domain name. For example, www.ggoogle.com and www.gooogle.com
Adjacent Character Swap
These typos are created by swapping the order of adjacent letters in the domain name. For example, www.googel.com and www.ogogle.com
Adjacent Character Replacement
These typos are created by replacing each letter of the domain name with letters to the immediate left and right on the keyboard. For example, www.googke.com and www.goohle.com
Double Character Replacement
These typos are created by replacing identical, consecutive letters of the domain name with letters to the immediate left and right on the keyboard. For example, www.gppgle.com and www.giigle.com
Adjacent Character Insertion
These typos are created by inserting letters to the immediate left and right on the keyboard of each letter. For example, www.googhle.com and www.goopgle.com
Missing Dot
These typos are created by omitting a dot from the domainname. For example, wwwgoogle.com and www.googlecom
Strip Dashes
These typos are created by omitting a dash from the domainname. For example, www.domain-name.com becomes www.domainname.com
Singular or Pluralise
These typos are created by making a singular domain plural and vice versa. For example, www.google.com becomes www.googles.com and www.games.co.nz becomes www.game.co.nz
Common Misspellings
Over 8000 common misspellings from Wikipedia. For example, www.youtube.com becomes www.youtub.com and www.abseil.com becomes www.absail.com
Vowel Swapping
Swap vowels within the domain name except for the first letter. For example, www.google.com becomes www.gaagle.com.
Homophones
Over 450 sets of words that sound the same when spoken. For example, www.base.com becomes www.bass.com.
Bit Flipping
Each letter in a domain name is an 8bit character. The character is substituted with the set of valid characters that can be made after a single bit flip. For example, facebook.com becomes bacebook.com, dacebook.com, faaebook.com,fabebook.com,facabook.com, etc.
Homoglyphs
One or more characters that look similar to another character but are different are called homogylphs. An example is that the lower case l looks similar to the numeral one, e.g. l vs 1. For example, google.com becomes goog1e.com.
Wrong Top Level Domain
For example, www.trademe.co.nz becomes www.trademe.co.nz and www.google.com becomes www.google.org Uses the 19 most common top level domains.
Wrong Second Level Domain
Uses an alternate, valid second level domain for the top level domain. For example, www.trademe.co.nz becomes www.trademe.ac.nz and www.trademe.iwi.nz
Supported Keyboard Layouts
Keyboard layouts supported are:
- QWERTY
- AZERTY
- QWERTZ
- DVORAK
Is the domain valid?
URLCrazy has a database of valid top level and second level domains. This information has been compiled from Wikipedia and domain registrars. We know whether a domain is valid by checking if it matches top level and second level domains. For example, www.trademe.co.bz is a valid domain in Belize which allows any second level domain registrations but www.trademe.xo.nz isn't because xo.nz isn't an allowed second level domain in New Zealand.
Popularity Estimate
URLCrazy pioneered the technique of estimating the relative popularity of a typo from search engine results data. By measuring how many times a typo appears in webpages, we can estimate how popular that typo will be made when users type in a URL.
The inherent limitation of this technique, is that a typo for one domain, can be a legitimate domain in its own right. For example, googles.com is a typo of google.com but it also a legitimate domain.
For example, consider the following typos for google.com.
| Count. | Typo |
|---|---|
| 25424 | gogle.com |
| 24031 | googel.com |
| 22490 | gooogle.com |
| 19172 | googles.com |
| 19148 | goole.com |
| 18855 | googl.com |
| 17842 | ggoogle.com |
Known Issues
Macos File Descriptor Limit
If DNS resolution fails under Macos it could be due to the small default file descriptor limit.
To display the current file descriptor limit use:
$ ulimit -aTo increase the file descriptor limit use:
$ ulimit -n 10000URLCrazy Appearances
Kali Linux
URLCrazy was a default tool in BackTrack 5, and later Kali Linux. https://tools.kali.org/information-gathering/urlcrazy
The Browser Hacker's Handbook
Authored by Wade Alcorn, Christian Frichot, and Michele Orru.
URLCrazy is included in Chapter 2 of this seminal work on the topic.
PTES Technical Guidelines
Penetration Testing Execution Standard (PTES) is a standard designed to provide a common language and scope for performing penetration testing (i.e. Security evaluations). URLCrazy is included in the Tools Required section.
http://www.pentest-standard.org/index.php/PTES_Technical_Guidelines
Network Security Toolkit
Network Security Toolkit is a bootable Linux distribution designed to provide easy access to best-of-breed Open Source Network Security Applications. https://www.networksecuritytoolkit.org/
See Also
URLCrazy was first published in 2009, and for many years was the most advanced opensource tool for studying typosquatting. Since then multiple other tools have been developed by the infosec community.
DNSTwist
DNSTwist is developed by Marcin Ulikowski and first published in 2015. DNSTwist had a significant feature overlap with URLCrazy at the time, and introduced many new features.
Language: Python
https://github.com/elceef/dnstwist
URLInsane
URLInsane was developed by Rangertaha in 2018 and claims to match the features of URLCrazy and DNSTwist.
Language: Go
https://github.com/cybint/urlinsane
DomainFuzz
DomainFuzz was developed by monkeym4sterin 2017. Language: Node.JS
https://github.com/monkeym4ster/DomainFuzz
Authors and Acknowledgement
- Authored by Andrew Horton (urbanadventurer).
- Thanks to Ruby on Rails for Inflector which allows plural and singular permutations.
- Thanks to Wikipedia for the set of common misspellings, homophones, and homoglyphs.
- Thanks to software77.net for their IP to country database
Community
If you have any questions, comments or concerns regarding URLCrazy, please consult the documentation prior to contacting one of the developers. Your feedback is always welcome.
via KitPloit
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
Related word
How Do I Get Started With Bug Bounty ?
How do I get started with bug bounty hunting? How do I improve my skills?
These are some simple steps that every bug bounty hunter can use to get started and improve their skills:
Learn to make it; then break it!
A major chunk of the hacker's mindset consists of wanting to learn more. In order to really exploit issues and discover further potential vulnerabilities, hackers are encouraged to learn to build what they are targeting. By doing this, there is a greater likelihood that hacker will understand the component being targeted and where most issues appear. For example, when people ask me how to take over a sub-domain, I make sure they understand the Domain Name System (DNS) first and let them set up their own website to play around attempting to "claim" that domain.
Read books. Lots of books.
One way to get better is by reading fellow hunters' and hackers' write-ups. Follow /r/netsec and Twitter for fantastic write-ups ranging from a variety of security-related topics that will not only motivate you but help you improve. For a list of good books to read, please refer to "What books should I read?".
Join discussions and ask questions.
As you may be aware, the information security community is full of interesting discussions ranging from breaches to surveillance, and further. The bug bounty community consists of hunters, security analysts, and platform staff helping one and another get better at what they do. There are two very popular bug bounty forums: Bug Bounty Forum and Bug Bounty World.
Participate in open source projects; learn to code.
Go to https://github.com/explore or https://gitlab.com/explore/projects and pick a project to contribute to. By doing so you will improve your general coding and communication skills. On top of that, read https://learnpythonthehardway.org/ and https://linuxjourney.com/.
Help others. If you can teach it, you have mastered it.
Once you discover something new and believe others would benefit from learning about your discovery, publish a write-up about it. Not only will you help others, you will learn to really master the topic because you can actually explain it properly.
Smile when you get feedback and use it to your advantage.
The bug bounty community is full of people wanting to help others so do not be surprised if someone gives you some constructive feedback about your work. Learn from your mistakes and in doing so use it to your advantage. I have a little physical notebook where I keep track of the little things that I learnt during the day and the feedback that people gave me.
Learn to approach a target.
The first step when approaching a target is always going to be reconnaissance — preliminary gathering of information about the target. If the target is a web application, start by browsing around like a normal user and get to know the website's purpose. Then you can start enumerating endpoints such as sub-domains, ports and web paths.
A woodsman was once asked, "What would you do if you had just five minutes to chop down a tree?" He answered, "I would spend the first two and a half minutes sharpening my axe."
As you progress, you will start to notice patterns and find yourself refining your hunting methodology. You will probably also start automating a lot of the repetitive tasks.
These are some simple steps that every bug bounty hunter can use to get started and improve their skills:
Learn to make it; then break it!
A major chunk of the hacker's mindset consists of wanting to learn more. In order to really exploit issues and discover further potential vulnerabilities, hackers are encouraged to learn to build what they are targeting. By doing this, there is a greater likelihood that hacker will understand the component being targeted and where most issues appear. For example, when people ask me how to take over a sub-domain, I make sure they understand the Domain Name System (DNS) first and let them set up their own website to play around attempting to "claim" that domain.
Read books. Lots of books.
One way to get better is by reading fellow hunters' and hackers' write-ups. Follow /r/netsec and Twitter for fantastic write-ups ranging from a variety of security-related topics that will not only motivate you but help you improve. For a list of good books to read, please refer to "What books should I read?".
Join discussions and ask questions.
As you may be aware, the information security community is full of interesting discussions ranging from breaches to surveillance, and further. The bug bounty community consists of hunters, security analysts, and platform staff helping one and another get better at what they do. There are two very popular bug bounty forums: Bug Bounty Forum and Bug Bounty World.
Participate in open source projects; learn to code.
Go to https://github.com/explore or https://gitlab.com/explore/projects and pick a project to contribute to. By doing so you will improve your general coding and communication skills. On top of that, read https://learnpythonthehardway.org/ and https://linuxjourney.com/.
Help others. If you can teach it, you have mastered it.
Once you discover something new and believe others would benefit from learning about your discovery, publish a write-up about it. Not only will you help others, you will learn to really master the topic because you can actually explain it properly.
Smile when you get feedback and use it to your advantage.
The bug bounty community is full of people wanting to help others so do not be surprised if someone gives you some constructive feedback about your work. Learn from your mistakes and in doing so use it to your advantage. I have a little physical notebook where I keep track of the little things that I learnt during the day and the feedback that people gave me.
Learn to approach a target.
The first step when approaching a target is always going to be reconnaissance — preliminary gathering of information about the target. If the target is a web application, start by browsing around like a normal user and get to know the website's purpose. Then you can start enumerating endpoints such as sub-domains, ports and web paths.
A woodsman was once asked, "What would you do if you had just five minutes to chop down a tree?" He answered, "I would spend the first two and a half minutes sharpening my axe."
As you progress, you will start to notice patterns and find yourself refining your hunting methodology. You will probably also start automating a lot of the repetitive tasks.
Related links
Tuesday, June 9, 2020
How To Download Torrents Files Directly To Your Android Device
uTorrent, one of the most popular BitTorrent clients, is now available for Android smartphones and tablets. Its use on mobile devices is very similar to its use in the PC. All you need is to search for torrents using the web browser on your mobile device, then uTorrent will download the files.
Procedure:
- Download and install uTorrent on your smartphone or tablet
- At the end of the installation click Open.
- Look for the torrents of your choice, several free and legal resources are available:
- http://www.legittorrents.info/
- http://www.publicdomaintorrents.info/
- http://www.legaltorrents.com/
- In the list of results, click on the magnet shaped button that appears below the file you want to download
- A window showing where the file will be saved in the memory card will open. Click on Add
- Utorrent will start downloading the file
- Once the download is complete press the Play button to open the file
Other softwares
Related posts
Any Indian DigiLocker Account Could've Been Accessed Without Password
The Indian Government said it has addressed a critical vulnerability in its secure document wallet service Digilocker that could have potentially allowed a remote attacker to bypass mobile one-time passwords (OTP) and sign in as other users to access their sensitive documents stored on the platform. "The OTP function lacks authorization which makes it possible to perform OTP validation with
via The Hacker News
via The Hacker News
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
Related word
Subscribe to:
Comments (Atom)